While at Black Hat this year I attend a great talk by security researcher Aditya K Sood. He discussed at length, the Fundamental Weaknesses in Botnet C&C Panels. One of the major talking points he hit on was the major use of Google Dorks (What are google dorks?). Dorks are based on the default design of the botnet family and like many other attack tools out there, they allow the user to change many of the default settings, but, come on, who really has time to change the default setting anyway? Luckily many botnet owners don’t.
Now, I know we’ve blogged about various ways to detect C&C operations in the past (such as Emerging BitCoin Theft Campaign) or CryptoLocker and if you’re a LogRhythm customer, you already have access to all of the out-of-box correlation rules. However, I don’t think you can have too many tools in your malware detection arsenal when it comes to defending your network. We all know the SeaHawks didn’t beat the Broncos in the Superbowl by having just one strategy in their defensive playbook. So here’s a quick reference table on common botnet families and their potential Google dorks
| **BotNet Family** | **Potential Google Dorks** |
| Zeus | Inurl: “cp.php?m=login” | inurl: “cp.php?letter=login” |
| ICE 1X | Inurl: “adm/index.php?m=login” |
| Citadel | Inurl: “cp.php?m=login” |
| BetaBot | Inurl: “login.php” intext: “myNews Content Manager” |
| SpyEye | Inurl: “frmcp/” |
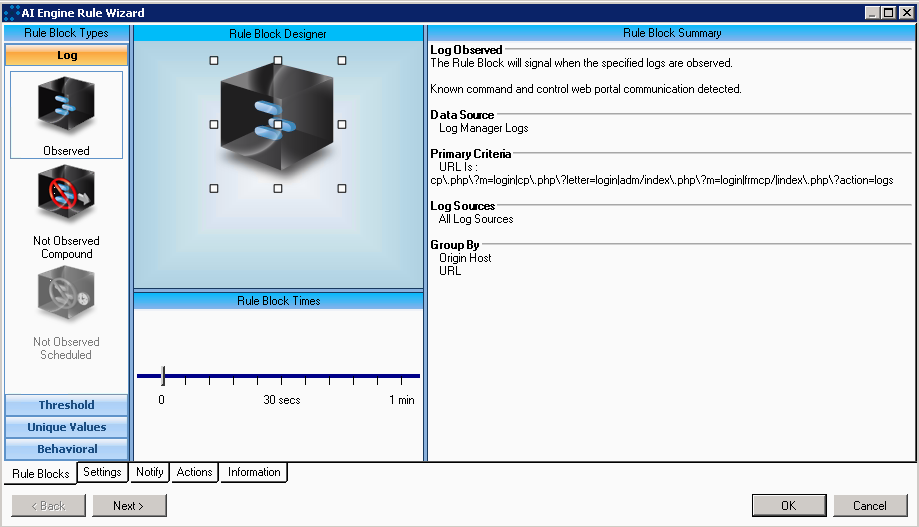
| And for good measure here is how to build automatic detection & alarming for communication with these C&C web portals in LogRhythm’s AI Engine. The key piece of this alarm is setting a regex pattern match on the URL Meta data field. Here is that regex: cp.php\?m=login | cp.php\?letter=login | adm/index.php\?m=login | frmcp/ | index.php\?action=logs |