When attackers are trying to break through your perimeter or are operating within your environment, you need to act quickly. Security intelligence is paramount. The good news is that you can detect most indicators of a threat from within the network.
Although NetMon is very easy to use, it can still provide an extremely powerful method for analyzing network traffic and finding security risks.
Application and Packet Capture
One of NetMon’s strongest features is its ability to categorize and extract relevant metadata for hundreds of network applications. To see a full list, check out the Applications Guide. This should help to identify interesting applications for tracking.
[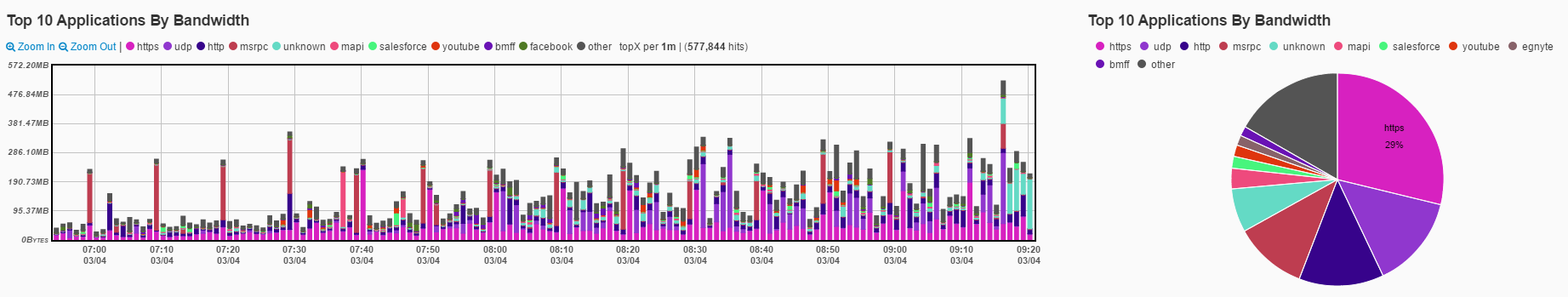
With this knowledge, deciding what applications to save as packet capture (PCAP) becomes much simpler. Ideally, everything could be stored, but obviously disk space is a limiting factor — in the event of an incident, if the network data has aged off, it’s going to complicate your investigation.
That’s why it’s wise to select several noteworthy applications. To do so, go to the Configuration tab and click on the ‘Capture’ button. There, applications can be added individually by name.
Example applications that would be useful to capture include DNS, HTTP, FTP, SMTP, TCP, and UDP.
Once captured, you can download PCAPs from the Analyze or Capture tabs. You can also use one of available scripts to retrieve them via the API, including a SmartResponse™ Plugin that can do so directly from the SIEM.
Query and Analyze Data
Beyond the Dashboard tab, another important feature of Network Monitor is the Analyze tab. Not surprisingly, the tab is the best place to conduct network analysis. The Query bar and Events Table are really the most important aspects of this view.
Finding relevant data is one of the most important capabilities that NetMon has. But it’s also one area left mostly to the user, and that makes basic knowledge of Lucene Query Syntax necessary.
Fortunately, it’s very easy—any time you’ve run a Google search, you’ve used Lucene. In NetMon’s case, simply putting text in the Query bar, anything from an IP to a string, will search all parsed metadata within the timeframe specified in the time bar. For example, searching the IP “10.0.0.2” will show ever session where that IP was parsed — as the source IP, destination IP, or anything else.
For example, searching the IP “10.0.0.2” will show ever session where that IP was parsed — as the source IP, destination IP, or anything else. But let’s say we want to be very specific and only want to show when our IP is the session’s source. The first step is to look at the Fields window — here, all of the metadata fields will be listed (checking the box next to a field will result in that field and its values appearing in the Events Table).
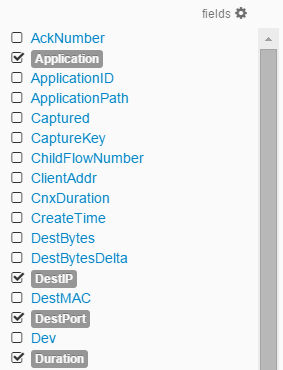
The field we want to search is SrcIP. Lucene has a very simple syntax for key/value pair matching: SrcIP:10.0.0.2. To combine pairs, use “AND”: SrcIP:10.0.0.2 AND application: http. For search within a range, use the TO operator and brackets: SrcIP:[10.0.0.2 TO 10.0.0.10]
Note that Boolean operators must be in all caps: OR, AND, AND NOT, and TO. Also remember, the timeframe for the search must be set using the time toolbar.
A good example of a commonly used, simple query is to find captured traffic from a specific host. Let’s imagine that Telnet traffic is observed from host user1.company.com—a definite security concern. Because Telnet is unencrypted, we can find and observe the actual text being transferred with NetMon, assuming that Telnet is being captured. Use the Query: host:user1.company.com AND application:telnet AND captured:true to show sessions that were saved. To perform some additional analysis on the host’s traffic, remove the application to see all captured traffic to and from the host. Perhaps we might find something suspicious and realize that the host was compromised.
Use Case:
The syntax also supports basic wildcards. An example of this query might be to find certain files exiting the network. The query
Filename:*.*pdf will find all PDFs that are indexed within a field in NetMon. We can add this to a more complex string to find all PDFs sent via SMTP* as attachments to email addresses outside of our organization’s domain. Application:smtp AND AttachSize:>1 AND Filename:*.pdf AND -Receiver:organization.com. If we know the name of a specific sensitive file that we don’t want to see, we can obviously change the Filename value.
Note: When searching for special characters, make sure to escape them with a backslash. For example, to search for “over-and-out”, the dashes are special characters and must be escaped: “over\-and\-out”.
Phishing schemes may use a fake sender address to more easily fool their victims. However, the emails still have to leave from a sender domain, and that creates a discrepancy between the sender email and sender domain. To find this in NetMon, use the following query:
Phishing schemes may use a fake sender address to more easily fool their victims. However, the emails still have to leave from a sender domain, and that creates a discrepancy between the sender email and sender domain. To find this in Network Monitor, use the following query:
SenderEmail:*organization* AND NOT SenderDomain:*organization.com* AND _exists_:SenderDomain
Applications may use common network ports to try and hide their traffic among well-known protocols. This technique is often seen by malware trying to maintain a covert channel to a victim. This is known as Port Misuse, and can be easily detected in NetMon. For example, to detect non-SSH traffic on port 22, use the following query:
Destport:22 AND NOT Application:ssh
Customized Layouts and Alarms
For many queries that are used often, it’s a good idea to customize the layout to better fit the data present for that application. This will give an analyst a clear and efficient workflow for churning through the data.
For example, for a Query meant to identify phishing via SMTP, use the Fields selector to specify important metafields while weeding out the noise: TimeStart, Receiver, Sender, SenderDomain, AttachSize, Filename, and MessageSize. Additionally, the Table can be expanded to the width of the page so that the data fits and is easily. After the layout is ready, save it using the Layout Control widget.
Finally, regular queries can be turned into alarms that will fire from within NetMon. These can be easily configured and monitored from
the Alarms tab.