“Start by doing what is necessary, then do what it possible; and suddenly you are doing the impossible.” – St. Francis of Assisi
In my 3+ years as a LogRhythm Professional Services & Security Consultant, I have often found customers with an appetite for security awareness, and the abilities to “look for the big things”, yet unable to satisfy their hunger.
Building the foundation: The security intelligence platform
From a traditional viewpoint, SIEM is typically classified as “Log Management”, but this is only a small portion of an effective SIEM. Log Management itself, is only one facet of true Security Management. In order to achieve a true Security Intelligence Platform, we need to include components such as Server Forensics, Network Forensics and Endpoint Forensics. Bundle up all this data, information, management and analytics and you are getting a much better picture of how SIEM has evolved into Security Analytics.
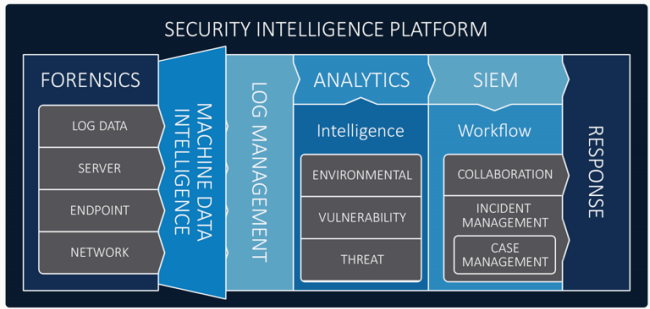
As a precursor to this, if you’ve never heard of LogRhythm’s Security Operation Maturity Model, or would like to read up about it, then I recommend reading the white paper available here.
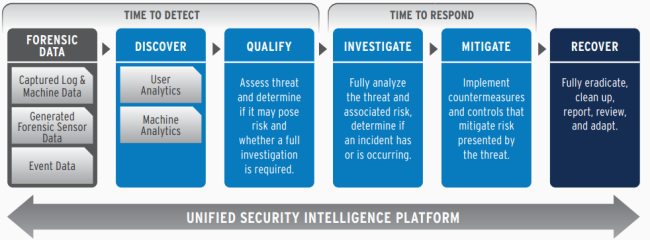
Essentially, the model empowers users of the LogRhythm Security Intelligence platform to increase their awareness around the activity in their infrastructure, thus reducing the time taken to identity a potential threat, indicators of a breach or anomalous behaviour in their infrastructure. This resulting insight and visibility, reduces the overall mean time to detect (MTTD) and enhances the security posture of the organisation.
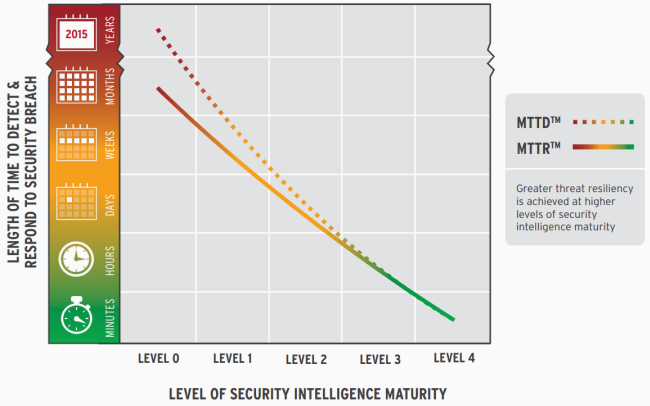
This lowered MTTD allows an organisation to better respond to whatever situation arose and consequently detected. Thus, the MTTR (mean-time-to response) is improved as well, due to the higher level of security intelligence leading to a far more rapid and effective decision making and response process.
Doing what is necessary: Base threat analytics
To address the fundamental requirement of “start by doing what is necessary”, LogRhythm developed a packaged module of rules around Base Threat Analytics using out-of-the-box features and intelligence to set up this foundation for implementation of Security Intelligence.
These rules have been designed to use LogRhythm’s AI Engine to detect correlations across various log sources, grouped into categories such as account anomalies, network anomalies, host anomalies and typical indicators of a compromise. Thus, the Base Threat Analysis suite encapsulates the “necessary” step for Security Intelligence.
From here, organizations need to begin to look at “What is possible?” Once the Base Threat Analytics module has been successfully implemented, the groundwork has been laid for an effective Security Intelligence posture.
The MTTD will already be greatly reduced, as the enhanced capabilities provided by LogRhythm’s AI Engine are able to effectively correlate and identify security, operational and audit anomalies and scenarios that would be far too time consuming or impossible due to the sheer volume of information required.
Explore the possibilities: Identifying the next step in your security intelligence maturity
So just what is possible? How does an organisation determine a direction from here? Should your security posture be driven by management decisions or perhaps by device and equipment types available to you? What about projects or newer generations and iterations of devices? Should they dictate your next phase in Security Intelligence Maturity?
The truth is, it can often be a combination of all of these factors, as well as a multitude more LogRhythm can help not only with guiding those decisions, but also in ensuring a mapping and planning of the future direction is outlined, enabling you to reach a much higher level of security awareness and intelligence.
The beauty of this is that LogRhythm’s scalable platform is designed that these additional modules and evolutionary phases of the Security Operations Maturity Model can be implemented rapidly and effectively on your existing platform. All the building blocks and tools are provided for you, with LogRhythm Professional Services helping you to understand how these fit together and the best ways to implement these tools.
Doing the impossible: Rapidly identifying and responding to threats
Finally, we are now doing the (seemly) impossible. We have managed to implement a Security Intelligence model that has helped to decrease the MTTD from a manual, labour-intensive and slow process to a more rapid, dynamic and intuitive process. This enables you to identify and understand complex scenarios and indicators of threats and breaches within minutes of them occurring.
The result? Because of this increased awareness, your MTTR has also decreased as you have the information needed to make quick, rapid and well-informed decisions on how best to respond to the incidents that have been identified.